Most cloud providers have a huge vulnerability and it's up to businesses to close this big security gap. Sound scary? It is. But it does not have to be.
Let's call these cloud services the big 3: Microsoft, Google, and Dropbox. Chances are that just about every business today is using at least one of them, either knowingly (the company has moved to it) or unknowingly (several employees or teams are doing so without corporate involvement). All three offer robust services that are inexpensive, simple, and reliable. But there's one huge security hole that, by default, leaves many firms wide open to an attack.
Perhaps you've seen something like this:
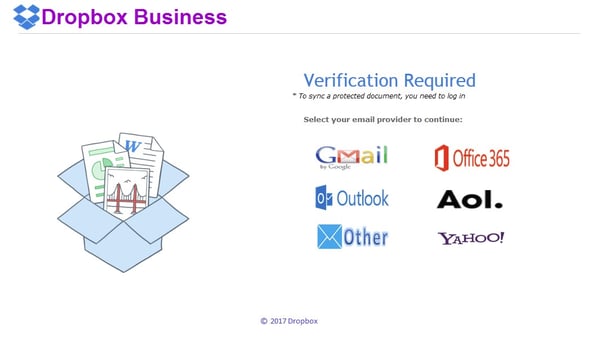 In case you are not already familiar with this type of phishing attempt, it goes like this: you receive an email that appears to be from someone you know with an action requiring you to click a link. The link asks you to sign in with your preferred cloud credentials, typically Microsoft Office 365, Gmail, Facebook, or Dropbox.
In case you are not already familiar with this type of phishing attempt, it goes like this: you receive an email that appears to be from someone you know with an action requiring you to click a link. The link asks you to sign in with your preferred cloud credentials, typically Microsoft Office 365, Gmail, Facebook, or Dropbox.
Once you enter your private credentials to this seemingly legitimate website, the scammer now has access to everything you store in that cloud service. We've seen some pretty scary stuff, from deleting or holding data hostage, to stealing customer lists and trade secrets, to getting bank wire transfers executed. For more information on phishing, please read our recent blog post, Security Update: Office 365 Phishing Attempts.
What's worse, this can happen without the phishing email altogether. Clever hackers sit anywhere there’s a public Wi-Fi network – a coffee shop, hotel, airport lounge, or park – and run a program throughout the day to scan each computer on the network looking for vulnerabilities that allow them to automatically "sniff" data from the machine. Throughout the day, they collect usernames and passwords. If this sounds alarming, that's because it is.
This is happening for one simple reason: so much of the world uses these same 3 cloud services that are easy to use and accessible from any device via a standard front-end. Usernames are most often your primary email address, so there's no guesswork there.
In the pre-cloud days, every company had a different system with different levels of access, login pages, and configurations. As an example, if the wrong person learned my corporate login credentials, they still may not know how to access our email, file system, or applications due to the fact that access required knowing where to log in and what settings to use. Today, the login pages for Google apps, Office 365, and Dropbox are all well known.
So what do we do? Going "off the cloud" is generally not a wise move – that's like getting rid of your car because it was broken into one time. Avoiding public Wi-Fi is a hard choice to live with (I'm typing this from an airport lounge, using their Wi-Fi). Training your staff in proper security precautions is important, but not foolproof as even the best trained person can slip up from time to time. Security systems, such as spam filtering and content security, are all necessary to block these messages, but they will never be 100% effective. It's normal and common for a few phishing messages to slip through. This is where two factor authentication (2FA) comes in.
2FA solutions require you to re-authenticate through a second means after your initial login – usually by confirming a temporary PIN code on your smartphone – to ensure that you really are who you say you are. Without this secondary form of authentication, you will not be granted access to your cloud. Many banks and financial services use 2FA, and it’s becoming more common with business, both large and small.
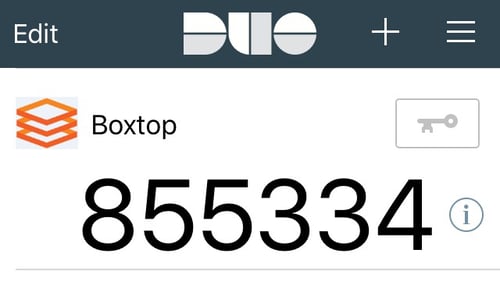 Our Solution
Our Solution
We're proud that Boxtop Premium, an enhancement to our popular Boxtop cloud solution, includes 2FA along with other security enhancements, such as data-at-rest encryption, email link filtering, attachment sandboxing, and extended data retention policies. Combined, these help ensure that a firm's entire IT infrastructure – from its applications to data – is fully secured and protected, and that our clients can help meet or exceed any security requirements they may have, including HIPAA, FINRA, NIST, and other compliance standards.
Since we developed Boxtop a few years ago, it has become a mission critical solution for companies who need better security for themselves and their clients. Tabush Group takes security seriously, and with Boxtop, we can provide that security while also simplifying IT for our clients. Boxtop enables companies to move their entire IT to the cloud and so that they can forget about their IT headaches and instead, concentrate on growing their business.
Learn more about Boxtop and request a free demo.








